Blockchain is known for its unique features, like end-to-end immutability, optimal security and privacy, and many more that can’t be otherwise discovered in other forms of distributed ledger technologies. In fact, it is due to these cumulative reasons that blockchain is now being used for multifarious purposes beyond the initial purpose for which the concept was coined in the first place. From maintaining product details in the supply chain cycles to storing important customer information at banking institutions, blockchain has found extensive purpose across various industries where immutability, security, and distributed control are the main priorities. But today, we will focus on the security aspect of this distributed ledger technology, especially cryptography in blockchain.
In textbook terms, cryptography can be considered an encryption technique for masking data and enabling secured transactions between two nodes on the blockchain network. further details have been elaborated below so that you can grasp the concept of cryptography in blockchain and understand the source that backs the claim of offering optimal security and protection in terms of data.
What Is Cryptography and Its Key Aspects?
Cryptography relates to a series of practices and techniques that can help establish a secure communication channel and allow data transfer between two nodes on the blockchain network. To do so, it encapsulates or masks the information from unauthorized access, fraud, or tampering, thereby maintaining confidentiality, immutability, integrity, and authenticity of all data pieces. Cryptography can be further elaborated based on its key aspects, including:
- Encryption: It involves converting regular data, like plain text messages into a random bit sequence, known as cipher bits.
- Decryption: In decryption, the cipher bit gets converted back to the original plain text form by removing the masking layers initially implemented.
- Cipher: Ciphers or mathematical algorithms are used to convert plain text into cipher text.
- Key: A key can be considered as a small input message required to get an output from a cryptographic model or algorithm.
What Are the Major Types of Cryptography Practices Used in Blockchain?
Since blockchain is a distributed ledger technology often used for monetary transactions, security, and data privacy need to be maintained at the highest possible levels. Implementing a single type of cryptography won’t suffice and might create problems, especially if hackers or users with malicious intent predict the cryptographic algorithm. To ensure this doesn’t happen, blockchain networks usually utilize a combination of multifarious cryptography practices, which have been elaborated further below.
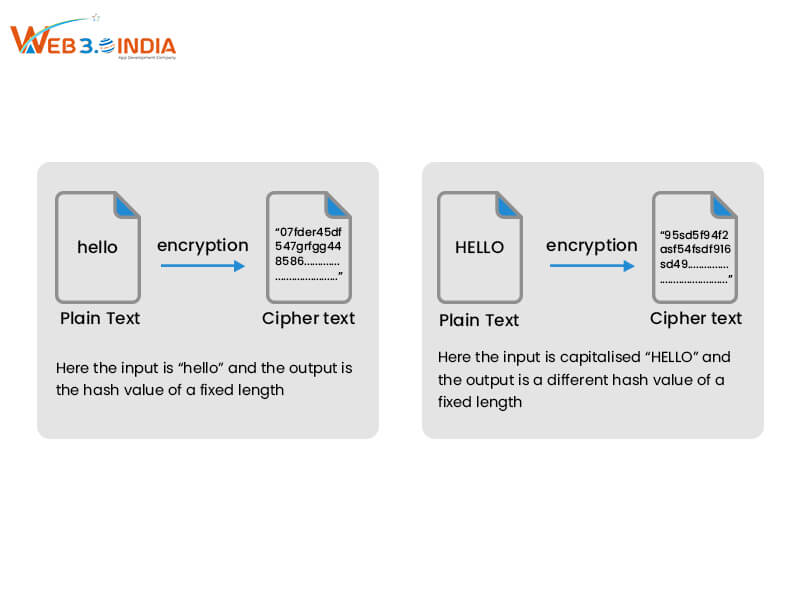
Hash Functions
Every transaction initiated on the blockchain network or the data blocks added to the distributed ledger is protected using hash codes. These are generated using hashing functions, which are designed to take a certain prompt input message and generate a random sequence of string, known as a hash code. These codes can’t be reversed to get the original text, which promises greater security. Also, no two systems will take different inputs and generate the same hash codes, thereby ensuring uniqueness and integrity. For instance, the SHA-256 hash function is used in Bitcoin currency for optimal protection and security.
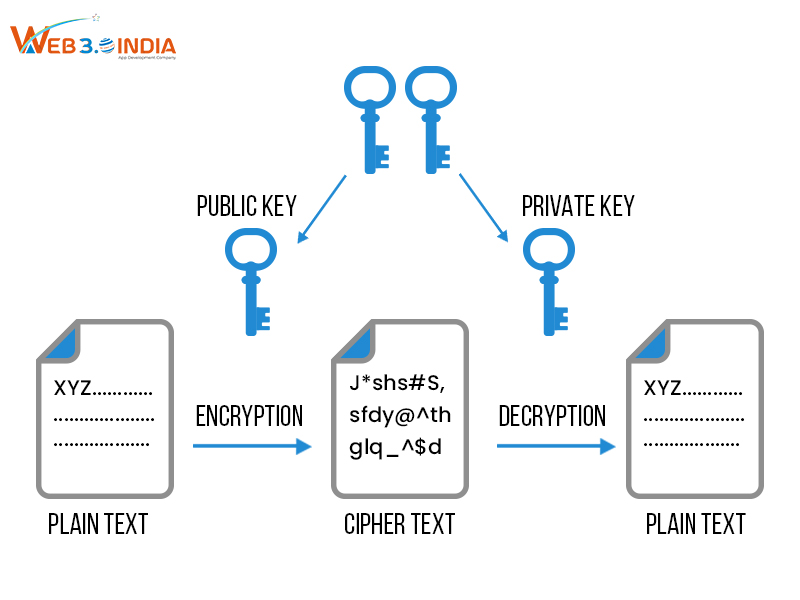
Public-Key Cryptography
Also known as asymmetric cryptography, it uses a pair of keys, known as the public and private keys. From the name itself, you can understand that public keys are exposed to the external world while private keys are restricted and confidential to individual users. Public keys are used for encrypting the data and sending it over the blockchain network. Once the transmission is completed, the prospective user will use the private key to decrypt and unearth the masked information. Asymmetric cryptography practices are often used for digital signatures, user identity management, and transaction security. One of the best examples is the ECDSA or Elliptic Curve Digital Signature Algorithm used in Ethereum and Bitcoin blockchains for transaction signing.
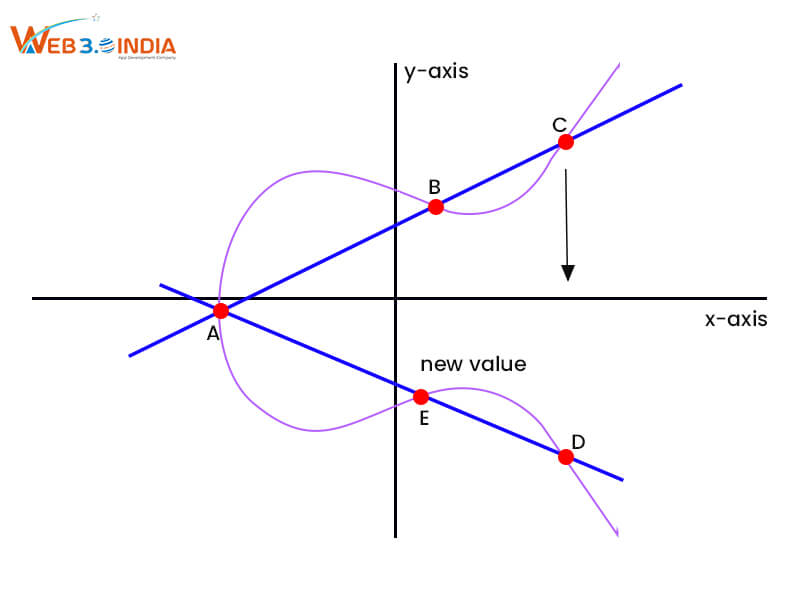
Elliptic Curve Cryptography
Since blockchain is a resource-constrained environment, a special type of asymmetric cryptography practice known as ECC or Elliptic Curve Cryptography is often implemented. Here, the elliptical algebraic structure is leveraged over finite fields to generate the keys having a much shorter size. ECC is usually used in areas where transaction verification and authentication have to be done at lightning speed along with facilitating key exchanges between different parties. The two major examples of Elliptic Curve Cryptography are ECDH or Elliptic Curve Diffie-Hellman and ECDSA or Elliptic Curve Digital Signature Algorithm.
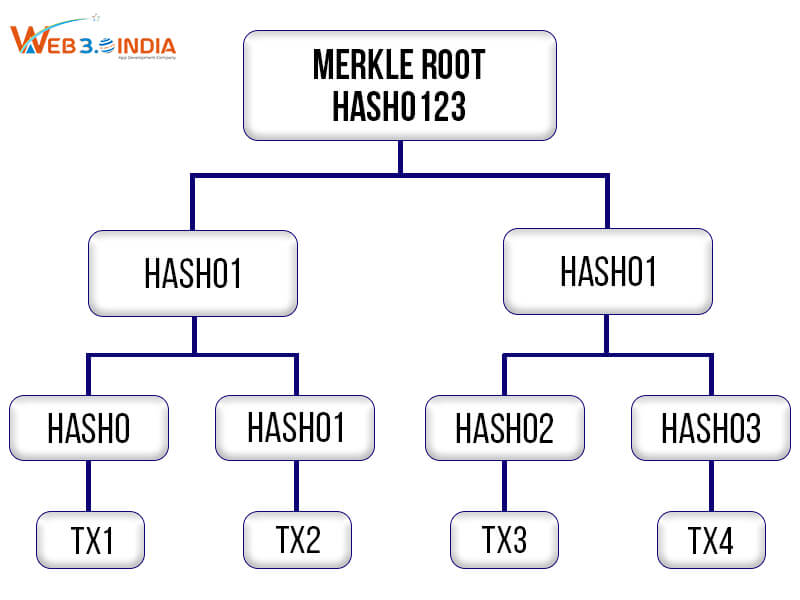
Merkle Trees
Merkle tree is also called a binary hash tree and is utilized to verify data integrity on the blockchain network. Every Merkle tree comes with a root that symbolizes a single hash used for representing the set of transactions to be added to the concerned block. The leaf node represents the transaction data hash while the non-leaf nodes are used to represent the hash of its child nodes, thereby establishing a connection with other blocks. Usually, the Merkle root is stored in the header block through which different nodes on the blockchain network can authenticate the integrity of all the transactions with ease.
What Is the Role of Cryptography in Blockchain System?
Understanding the role of cryptography in blockchain network is essential to ensure data is protected and kept secure from any unauthorized access, scam, and manipulation. In the below section, we have briefed some of how cryptographic practices have helped meet user expectations in the decentralized ecosystem.
Transaction Security
Every transaction initiated on the blockchain network is protected using different cryptographic functions. Once the transaction is recorded on the ledger, it becomes immutable and it’s not feasible to alter the details because that would require recalculating all the connected transactions through the hash root. Also, transactions can be made more secure using digital signatures where only the rightful owner of the private key can authorize the transaction and prevent any fraudulent activity.
Trust In The Decentralized Ecosystem
Since the decentralized ecosystem doesn’t have any central authority, cryptographic algorithms are used for verifying the transactions and user identities. There is no need to rely on any third party for maintaining transaction authenticity or relying on one another for initiating or authorizing a transaction. Apart from this, asymmetric cryptography enables users to leverage the public and private key pairs for encrypting and decrypting the information associated with any transaction initiated on the blockchain network.
Data Privacy And Confidentiality
Data privacy and confidentiality are maintained through two different cryptographic practices. Zero-knowledge proofs or ZKPs are used to verify transactions without revealing any sensitive information, like the sender’s and receiver’s identities and the amount being transferred. Also, pseudonymity is also used in the form of asymmetric cryptography where the public key is not tied to the real-world identity of the sender. Hence, receivers won’t be able to deduce the sender’s information even if the public key is exposed to the outer world.
Data Integrity
One of the many reasons for which cryptography is used in the blockchain network is to maintain data integrity. For instance, when the Merkle tree is used, the hash of a current block to be added to the ledger contains information on all the hash codes used in the previous block, thereby establishing a linked chain. If the hash is tampered with, it would change the very existence of the block, thereby triggering the system to reject the addition. Similarly, the Merkle tree root contains information about all the transactions, which further allows users to verify and maintain data integrity throughout.
Consensus Mechanisms
Whenever a new block has to be added to the distributed ledger of the blockchain or a new transaction has to be authorized, all the participating nodes with proper roles or access need to provide agreement through a specific consensus protocol. Blockchain utilizes numerous such consensus mechanisms, like Proof of Stake and Proof of Work, which are further based on cryptographic algorithms. For instance, in the Proof of Work consensus protocol, data miners need to solve a puzzle to generate the hash functions and authorize the addition of new blocks to the blockchain system.
Non-Repudiation
Digital signature is a common aspect of cryptography, which ensures that once a sender authorizes a transaction, he or she cannot deny accountability or responsibility for the same. Also, with the help of cryptography, all the recorded transactions can be audited efficiently without compromising data integrity and confidentiality. Owing to these reasons, blockchain is said to have optimal transparency throughout the ledger and maintain the immutability of the records being stored.
Protection Against Sudden Attacks
Last but not least, cryptography can also be used to protect the blockchain network from sudden cyber attacks. For instance, Sybil attacks are quite common and hard to prevent, especially since a single person creates multiple fake identities to gain access to a network. However, this can be prevented on the blockchain by implementing the use of digital signatures and a Proof of Work consensus mechanism.
Conclusion
Here, we have elaborated on the use of cryptography in blockchain systems to ensure optimal data confidentiality and integrity, ledger transparency, and user authenticity. Different types of cryptographic algorithms are implemented to ensure the blockchain network is immune to data forgery and manipulation, unauthorized ledger access, and data loss due to sudden network breaches.