The entire crypto market runs virtually. Fund holders and investors connect with the market through dedicated platforms. All the transactions are digitized and stored in the online blockchain ledger. Although this distributed ledger technology is highly secured, risks are prevalent in the industry. According to a report, 98.04% of cryptocurrency theft was due to hacking activities while the rest 1.96% was the result of fraud in 2024. So, securing crypto wallets is of the utmost importance for every user. Since all the operations are digital, cyber risks will be there. The only way to protect the funds is to secure the wallet properly.
Every crypto wallet has a pair of public and private keys. The public key serves as the wallet’s address, validating the anonymity principle. A private key, on the other hand, is a unique digital fingerprint. If it is hacked or known to others, your digital assets will be at risk. Activities like scams and phishing are some of the major reasons for crypto thefts worldwide. With this being said, we have compiled a list of practical tips for securing crypto wallets.
Types of crypto wallets and their security levels
Two major types of crypto wallets are in the market. Choosing the right one will help you secure your digital assets easily. Besides, the security measures differ depending on the wallet type you use. Hence, we have briefly illustrated the pros and cons of both these wallet categories for cryptocurrencies based on their security aspects.
Hot wallets
These crypto wallets remain connected to the internet throughout. You will be able to access your digital assets anytime remotely. Trading, buying, or selling cryptocurrencies become hassle-free and more convenient. Below are some of the examples of hot wallets.
- Web-based wallets: Can be accessed through marketplaces like Binance and Coinbase
- Mobile wallets: Need to be installed in the mobile as an application like MetaMask and Trust Wallet
- Desktop wallets: Can be installed on the desktop like Electrum and Exodus
Benefits of hot wallets
- These can be accessed from any device having internet access.
- Hot wallets come with an intuitive interface for users.
- These are suitable for fast and convenient crypto transactions.
Risks of hot wallets
- Since these need to be connected to the internet, hot wallets are vulnerable to hacking and phishing.
- The private key is at higher risk of being exposed.
Cold wallets
As the name sounds, cold wallets are offline crypto storage solutions. They keep digital assets protected from phishing and hacking activities since they do not remain connected to the internet. Some of the examples of cold wallets are:
- Hardware wallets or physical devices like Trezor and Ledger Nano
- Paper wallets having QR codes of the public and private keys
Benefits of cold wallets
- These are immune to online crypto thefts and phishing activities.
- Private keys remain within the user’s sole control. No third party will have access to these keys.
- These are convenient for holding crypto assets for prolonged periods.
Risks of cold wallets
- There will be risks of losing the physical devices.
- Once lost, you may lose your crypto funds permanently if no backup is there.
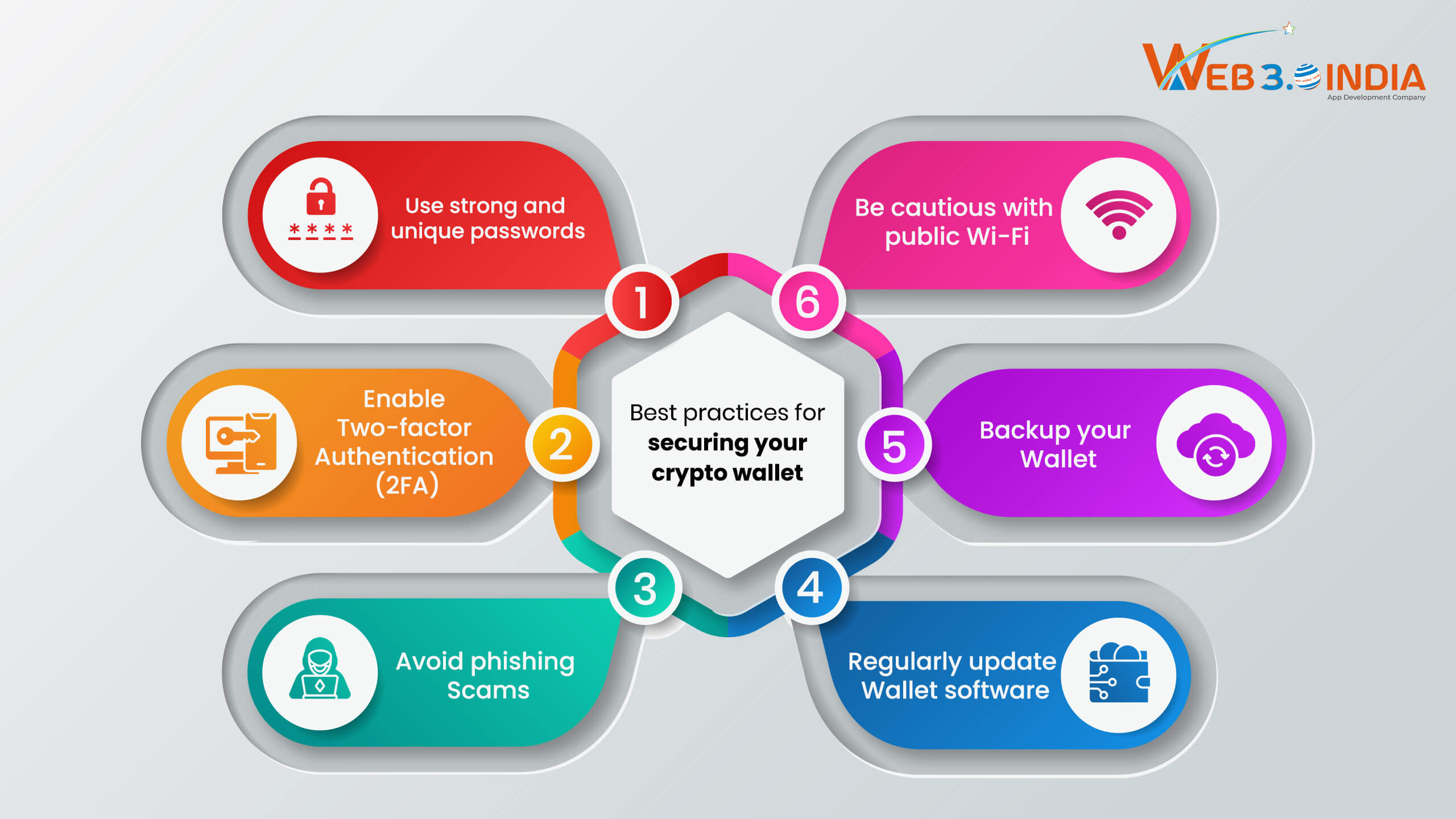
Best practices for securing your crypto wallet
Digital assets will always be at risk of being hacked or stolen. So, users should take proactive measures to secure crypto wallets. Only then can they protect their assets and trade with cryptocurrencies conveniently. The section below illustrates the best security practices for crypto wallets.
Use strong and unique passwords
The passwords for hot wallets should be strong and unique. For instance, if you give your birth date or any known password, it can be hacked easily. Passwords with weak to moderate strength are at higher risk of being exposed. That’s why opting for an alphanumeric password with a special character is more convenient. Although you may have difficulty remembering it, at least your digital assets will be protected.
Below are a few tips for creating strong wallet passwords.
- Use a combination of numbers and alphabets for securing crypto wallets.
- Do not use your name or any other known detail in the password.
- Avoid using your birth date in the password.
- Never store passwords on the browser or mobile phones, especially in the cache memory.
- If you use password managers, invest in licensed software.
Enable two-factor authentication (2FA)
Two-factor authentication or 2FA is the best way to secure crypto wallet. It requires wallet owners to complete two verification steps. Once verified, they can access their wallets and complete any transaction. Following are some of the benefits of enabling 2FA for crypto wallets.
- Since it requires double verification, unauthorized access can be eliminated.
- Hackers may get access to your password. However, they will still need the second verification factor to access your wallet.
- Thanks to double-layered security, crypto wallets remain protected.
Some of the best 2FA modes for securing crypto wallet are:
- Google Authenticator and Microsoft Authenticator generate time-sensitive verification codes.
- SMS-based 2FA will send the verification code directly to the mobile phone through a message.
- Hardware security keys can secure the authentication process, like Leder and YubiKey.
Avoid phishing scams
Phishing is the most common risk factor for crypto wallet owners. These are tricks that compel users to reveal their wallet passwords, seed phrases, and private keys. Some of the common phishing tactics and the ways to avoid them are:
- Fraudulent websites often mimic legitimate ones and gain access to the user’s login credentials. These usually have slight URL variations, be it in spelling or domain. So, always double-check the URL of the website before entering the login credentials.
- Sometimes, emails also contain malicious links. If clicked, these will lead you to fake sites automatically. For example, emails with unsolicited password requests or poor grammar can be considered as phishing attack. Do not click on the links present in the email.
- There are several fake and malicious crypto wallet apps in the market. Avoid downloading and using them for cryptocurrency transactions.
Regularly update wallet software
Most hot wallets come from the hands of third-party providers. Hence, keeping the software updated is the best way to secure crypto wallet. That’s because the updates released often contain security patches and fixes. These will help in eliminating the current security vulnerabilities at once. Besides, if you do not update the software, it will be at a higher risk of being hacked.
Backup your wallet
Always keep a backup of your private wallet key and the recovery phrases, if any. This will help you access your wallet even if you forget the password. Here are some ways to create wallet backups.
- Use physical backups.
- Metal plates with passwords engraved on them will be safer.
- Always encrypt your digital backups, if any.
Be cautious with public Wi-Fi
Public Wi-Fi can put your crypto wallet at a higher risk of being hacked. So, if you are accessing the local network, use a VPN for strong protection. It will make your device’s IP anonymous. Hence, hackers won’t be able to know the device’s details and access your wallet.
Advanced security tips for crypto enthusiasts
- Multi-signature protection is one of the best ways to secure crypto wallets. It requires multiple private keys to authorize a transaction.
- You can distribute your crypto funds across multiple wallets. This will help you reduce the security risks easily.
- Always verify your device’s security settings. Keep them updated periodically.
Conclusion
Here, we have discussed the best ways to secure crypto wallet. If you use passwords, ensure it is strong and unique. For best security, enable the 2FA in your wallet. Always create backups of your private keys and recovery phrases to avoid permanent loss of crypto assets. Using proactive security measures can make crypto transactions hassle-free for you.